Automate Total Log Retention of all tables in Microsoft Sentinel: From Tedious Manual Steps to Seamless Bulk Updates
In today’s cloud-first security landscape, operational efficiency is just as critical as threat intelligence. According to Forrester’s “State of Security Operations 2024,” nearly 65% of security teams cite time-consuming manual processes as a top roadblock to effective threat response. When compliance and security policies demand multi-year log retention, the task of updating hundreds of Sentinel tables individually can drag skilled analysts into hours of repetitive, error-prone work. This blog introduces a PowerShell script designed to automate this process, freeing up valuable time and resources.
Reality Check for Security Operations
- Is your SOC spending hours each quarter just setting total data retention policies of new tables or new table setup?
- Do auditors and compliance teams demand rapid, consistent evidence of log retention across all your workspaces?
- Ever worry that a missed click or oversight could lead to gaps in your data storage policy?
If any of these concerns hit home, it’s time to rethink your approach.

As regulatory expectations rise and cloud data grows, you might find yourself with 200+ analytic and custom tables in Microsoft Sentinel — each requiring a configured “total retention” period. Doing this by hand in the Azure Portal can:
- Consume precious staff hours
- Lead to inconsistent results
- Cause “change fatigue” in your security team
A large global bank recently estimated over 15 hours annually wasted on manual retention updates — just in a single workspace.
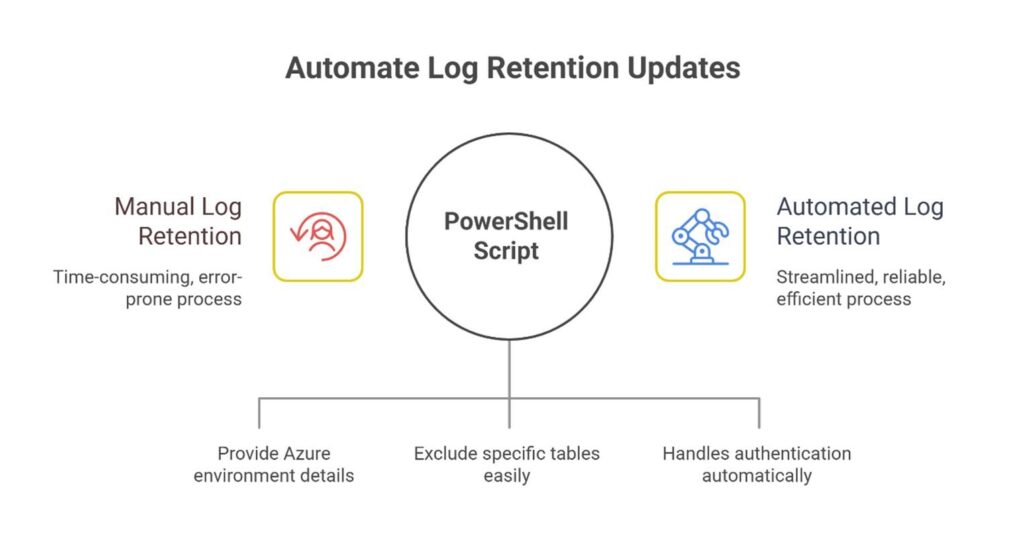
To empower your SOC and eliminate this manual burden, I’ve developed a robust, interactive PowerShell script. This script streamlines the process of updating total log retention of all the tables across your Microsoft Sentinel environment.
- Input your Azure subscription, resource group, Log Analytics workspace, and desired retention period — and the script will apply settings across all tables.
- Skip specific tables—want to retain only certain logs longer (or shorter)? Just supply their names and they’re automatically excluded.
- Token refresh logic ensures reliability — even for large environments, the script refreshes your Azure credentials in the background, preventing expiry errors.
Key Features & Benefits
- Bulk Automation: Update hundreds of tables in minutes, not hours.
- Zero Guesswork: Prompts for all needed information so no edits required.
- Flexible Exclusion: Easily skip system or custom tables when needed.
- Secure & Robust: Handles Azure authentication, token refresh, and error messaging.
User-Friendly Output: See exactly which tables were updated, skipped, or failed — for immediate operational clarity.
How It Works: Automated Total Retention of all tables in Action
- Step 1: Login to Azure Log in with Azure PowerShell for secure authentication and upload the script.
- Step 2: Run & Provide Details:
- Step 3: Customize Choose whether to skip any tables (simply enter a comma-separated list).
- Step 4: Push The script gathers your table list, loops through each, and sets retention — handling token refreshes automatically.
- Step 5: Review Results Success, skip, and error messages are color-coded and summarized in real-time.
Why This Matters
By blending automation with flexible policy controls, you ensure:
- Governance: Compliant retention across your entire Sentinel estate.
- Efficiency: Free up your engineers and analysts for threat hunting, not repetitive clicks.
Reliability: Consistent settings and robust error handling reduce risk of human oversight or missed updates.
Conclusion: Let Your Security Team Focus on What Matters
Manual retention management of all tables is a thing of the past. With this script, you can keep your Microsoft Sentinel deployment compliant, efficient, and reliably configured — with just a few prompts and no risk of missed tables. Empower your analysts to do what humans do best: investigate, respond, and defend — while automation takes care of the heavy lifting.
Ready to transform your Sentinel operations?
By: Pranjal Verma, Senior Technology Consultant, Microsoft Security, Inspira Enterprise





